Three Major Attacks in Two Years - Time to Put Our Engineers Hats On
"Ko e Otua mo Tonga ko hotau tofi'a" - God and Tonga are our inheritance King Tupou VI
The Reality Check We Needed
This is indeed a great start, we are finally heading in the right direction. Yes, in this day and age, Information Security (Infosec) is common practice. Moreover, we now have the Government's Digital Transformation and Cybersecurity Frameworks published online.
However, three official major attacks in 2+ years signifies that our greatest strength is still our weakest link i.e. the human aspect.
- TCC (Tonga Communications Corporation) - 2023 - Medusa ransomware
- MOH (Ministry of Health) - 2025 - INC Ransom attack
- TPL (Tonga Power Limited) - 2025 - Recent incident
Having said that, we have our policies in place, but we all know that adhering to policy discussions only camouflages technical incompetencies. Therefore, let's put our Engineers hats "ON" and dig deeper to find out our vulnerabilities as root causes of our problems.
The Harsh Truth - Policy ≠ Protection
While Tonga has made commendable progress in establishing cybersecurity frameworks and digital transformation policies, the stark reality is that paper shields don't stop digital bullets. Three major cyber attacks in just over two years isn't bad luck, it's a systemic failure of our cybersecurity infrastructure where both technical and human aspects are critical components.
The Attack Timeline - A Pattern Emerges
March 2023 - Tonga Communications Corporation (TCC)
- Attacker: Medusa ransomware group
- Impact: Administrative systems compromised, customer service disrupted
- Root Cause: State owned telecommunication infrastructure vulnerability
June 2025 - Ministry of Health (MOH)
- Attacker: INC Ransom group
- Impact: Complete National Health Information System shutdown
- Cost: US$1 million ransom demand (unpaid)
- Consequence: Manual paper records across all four hospitals
2025 - Tonga Power Limited (TPL)
- Details: Recent incident under investigation
- Concern: Critical infrastructure targeting continues
Technical Vulnerabilities - The Real Engineering Problem
Let's stop sugar-coating the situation with policy rhetoric and examine the actual technical deficiencies that enabled these attacks:
1. Legacy Infrastructure Exposure
The Problem: Some of Tonga's critical infrastructure relies heavily on outdated systems with known vulnerabilities.
Technical Reality:
- Unbatched Remote Desktop Protocol (RDP) vulnerabilities
- Heavy reliance on proprietary software stacks including Microsoft unpatched systems instead of taking a sovereignty approach with Linux, Open Office and Open Source solutions
- Insufficient network segmentation between critical systems
- Single points of failure across government networks
- Policy initiatives should be aligned accordingly so that what's on paper is aligned with what is installed
Engineering Solution Required: Complete infrastructure modernization with zero-trust architecture.
2. Inadequate Network Security Architecture
The Problem: While our government network infrastructure is well designed with SOC team management and vendor independence, the challenge lies in continuous monitoring with proactive rather than reactive response capabilities.
Current Strengths:
- Government network operations, management, and security handled by our SOC team using Government Core network equipment
- Deliberately designed to be secure, scalable, and free from vendor lock-in
- One of the 2 major telecom providers provides fiber service but has no control over the Government network
- Seamless ability to switch to alternative fiber service providers
Technical Gaps to Address:
- Enhanced micro-segmentation within government networks
- Strengthened monitoring and intrusion detection capabilities
- Advanced endpoint detection and response (EDR) deployment
- 24/7 SOC capabilities expansion
Engineering Solution Required: Build upon our solid foundation with enhanced defense-in-depth, real time monitoring and automated response while maintaining our vendor independent approach.
3. Data Protection Failures
The Problem: Critical government data lacks proper encryption and access controls.
Technical Deficiencies:
- Unencrypted data at rest in government databases
- Weak authentication mechanisms (password only access)
- Insufficient backup and recovery capabilities
- No data loss prevention (DLP) systems
Engineering Solution Required: End-to-end encryption with hardware security modules and multi-factor authentication.
4. Incident Response Inadequacy
The Problem: When attacks occur, our response is reactive rather than proactive.
Operational Gaps:
- No automated incident response capabilities
- Dependence on external expertise (Australian cyber teams)
- Insufficient forensic capabilities for attack attribution
- Slow recovery times leading to extended service disruptions
Engineering Solution Required: 24/7 SOC with automated playbooks and local expertise.
The Pacific Context - Why Small Islands Are Prime Targets
Cyber criminals aren't randomly selecting Tonga, we represent an attractive target profile:
Target Characteristics
- Limited Cybersecurity Resources: Small and isolated CERT teams with limited resources but with huge responsibilities
- Critical Infrastructure Concentration: centralised systems controlling essential distributed services
- Geographic Isolation: Delayed incident response and limited local expertise
- Economic Vulnerability: Significant disruption from relatively small attacks
- Digital Transformation Rush: Rapid digitization without corresponding security investment
Regional Pattern Analysis
The attacks on Tonga mirror a broader Pacific trend:
- Vanuatu (2022): Complete government shutdown for over a month, ransomware attack on November 6, 2022
- Palau (2025): Ministry of Health compromise by Qilin ransomware group on February 17, 2025
Engineering Insight: Pacific Island nations need specialized cybersecurity architectures designed for geographic and resource constraints.
Engineering Solutions - Beyond Policy Papers
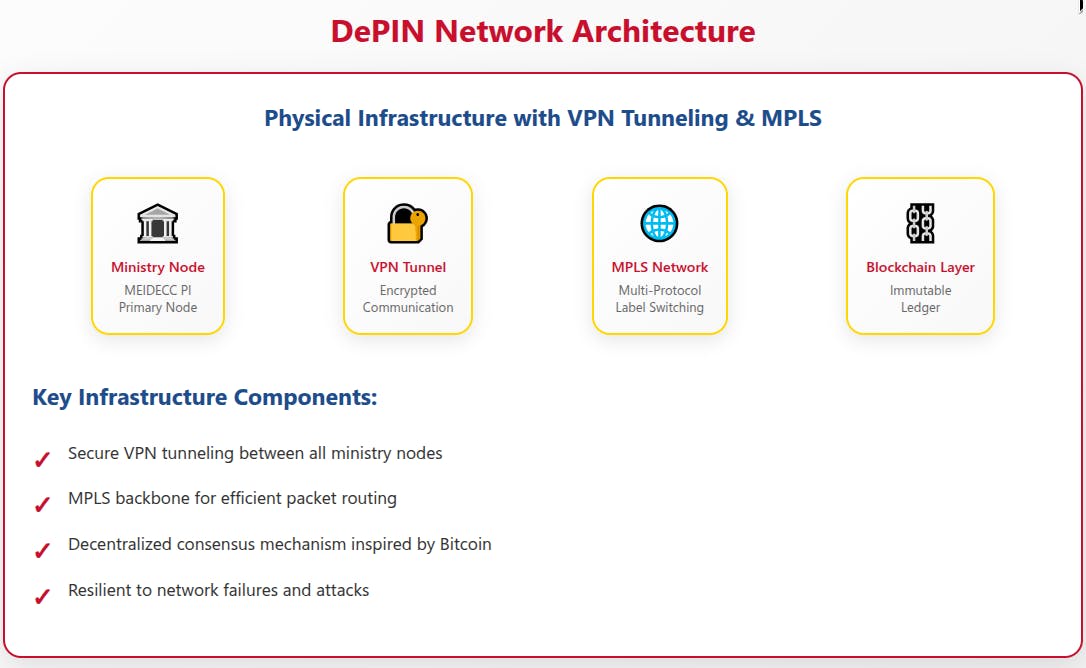
1. Implement Decentralized Physical Infrastructure Network (DePIN)
Technical Approach:
- Solar-Powered Blockchain Nodes: Energy independent security infrastructure
- Distributed Computing: No single point of failure across islands
- Hardware Security Modules: Physical cryptographic protection
- Satellite Backup Communications: Resilient connectivity during disasters
Advantage: Creates unhackable government infrastructure that operates independently even during power outages and natural disasters.
2. Zero-Trust Government Network Architecture
Implementation Strategy:
Citizen Access → API Gateway → Identity Verification →
Ministry Specific Networks → Encrypted Data Storage →
Immutable Audit Trail → Real-time Monitoring
Key Components:
- Multi-factor authentication for all access
- Continuous device and user verification
- Micro-segmented ministry networks
- Encrypted inter-ministry communications
3. Proof-of-Authority Blockchain for Government Services
Technical Benefits:
- 3-second transaction finality: Faster than traditional databases
- Immutable audit trails: Impossible to alter government records
- Smart contract automation: Reduces human error and corruption
- Distributed consensus: Multiple ministry validation required
4. AI-Powered Threat Detection and Response
Capabilities:
- Real-time network traffic analysis
- Behavioral anomaly detection
- Automated threat containment
- Predictive vulnerability assessment
The Cost of Inaction - Economic Reality
Direct Attack Costs
- MOH Attack Recovery: Estimated $500K+ in remediation costs
- TCC Administrative Disruption: Customer service delays and reputation damage
- Australian Cybersecurity Assistance: Ongoing dependency costs
Indirect Economic Impact
- Healthcare System Disruption: Immeasurable cost to public health
- International Reputation Damage: Reduced investor confidence
- Government Efficiency Loss: Manual processes replacing digital systems
Investment vs. Risk Calculation
DePIN Infrastructure Investment Summary:
- Total CAPEX: Estimated $200,000 USD for comprehensive cybersecurity infrastructure
- Annual OPEX: Estimated $100,000 USD for ongoing operations and maintenance
- Potential attack costs: $10,000,000+ USD in damages and recovery
ROI Analysis:
- CAPEX Protection Ratio: 50:1 ($10M potential costs ÷ $200K investment)
- Annual OPEX Protection Ratio: 100:1 ($10M potential costs ÷ $100K annual costs)
- Total 3-Year ROI: 12.5:1 ($10M potential costs ÷ $800K total 3-year investment)
Investment Strategy: Leveraging existing government assets (buildings, Starlink, network equipment) to minimize costs while maximizing security resilience through solar-powered, decentralized infrastructure.
Cost Optimization Through Digital Sovereignty:
- Existing infrastructure utilization: Leveraging current government network, buildings, and Starlink assets
- Zero-cost security: Linux iptables firewalls replacing expensive proprietary solutions
- Localized AI agents: Custom-trained models for Pacific Island threat patterns
- Local expertise development: Reducing dependency on expensive overseas consultants ($200K+/incident)
- Open source ecosystem: Eliminating proprietary software licensing fees (~$150K/year savings)
- Energy independence: Solar-powered infrastructure reducing operational costs (30-50% energy savings)
Recommendations - Engineering-First Approach
Immediate Actions (0-6 months)
- Top Priority: Modification and updates to current policies - Drive innovation and recommendations to align with technical realities
- Empowerment of Tonga CERT - Enhanced capabilities in both human and technical resources to become our first line of defense as in proactive response rather than reactive, more to empower our local expertise to handle our own defenses rather than always looking abroad to overseas consultants
- Awareness campaigns with capacity building - Upgrading our human resource cyber safety skills and cleanliness
- Emergency Security Assessment: Complete penetration testing of all critical systems
- Incident Response Team Enhancement: Strengthen local capabilities with international support agreements
- Critical System Isolation: Air-gap essential infrastructure from internet-facing systems
- Advanced Staff Cybersecurity Training: Technical skills development beyond basic awareness
Medium-term Implementation (6-18 months)
- DePIN Pilot Project: Start with MEIDECC as proof-of-concept
- Zero-Trust Network Deployment: Implement across core ministries
- SOC Establishment: 24/7 monitoring and response capabilities
- Backup Infrastructure: Distributed, encrypted, and regularly tested
Long-term Transformation (18-36 months)
- Complete Infrastructure Overhaul: DePIN-powered government network
- Blockchain Government Services: Immutable, transparent, and efficient
- Regional Cybersecurity Hub: Pacific Islands cooperation center
- Cybersecurity Workforce Development: Local expertise building
Update - Collaborative Engineering Consensus Reached
Following productive discussions with cybersecurity colleagues across government, we have reached consensus with the conclusion that our greatest strength is still our weakest link i.e. the human aspect.
Recommended Enhancement Areas:
Beyond Training:
- Add automated patch management and behavioral monitoring
- Implement continuous user verification systems
Network Segmentation:
- Consider micro-segmentation within ministries
- Deploy zero-trust internal architecture
SOC Capabilities:
- 24/7 threat hunting and automated incident response
- Proactive threat intelligence integration
Power and Backup Connectivity:
- Independent government solar micro grids
- Satellite backup options for total outage scenarios
The DePIN Implementation Path Forward
Looking ahead: The vendor independent approach aligns perfectly with the MEIDECC DSS and Performance Indicator Dashboard. This will demonstrate how distributed infrastructure can provide both resilience and independence from traditional vendor dependencies.
Our foundation is solid. We're moving from "adequate security" to "resilient security", which is exactly what we need given the targeted attacks we have experienced.
The government's scalable approach puts us in a great position for the DePIN infrastructure rollout.
Conclusion: Engineering Our Digital Sovereignty
The three major cyber attacks on Tonga revealed a fundamental truth i.e our greatest strength i.e. our human aspect is also our weakest cybersecurity link. But this collaborative engineering approach demonstrates that we can transform this challenge into innovation.
The engineering reality is now clear:
- Human factors remain our primary vulnerability
- DePIN infrastructure can provide technical resilience independent of human error
- Our vendor-independent architecture positions us for advanced implementation
- We have the team consensus needed for transformational change
The collaborative path forward:
- Implement automated systems to reduce human error impact
- Deploy DePIN infrastructure starting with MEIDECC
- Build resilient, energy-independent government networks
- Create the Pacific's most secure digital sovereignty model
As engineers and technologists working together, we have the opportunity to transform this crisis into the most innovative government infrastructure in the Pacific. The DePIN model will demonstrate that small island nations can achieve both digital sovereignty and cybersecurity resilience.
The question isn't whether we can afford to implement these solutions, it's whether we can afford not to lead this transformation.
"Ko e Otua mo Tonga ko hotau tofi'a" means our inheritance includes both our islands and our responsibility to protect them in the digital age. Let's stop talking about cybersecurity and start re-engineering it.
References
- CERT Tonga Ransomware Advisory (February 2023)
- CERT Tonga INC Ransomware Advisory (June 2025)
- The Record: Tonga Ministry of Health Cyberattack (June 2025)
- Cyber Daily: INC Ransom Attack Analysis (June 2025)
- The Record: Tonga Communications Corporation Attack (March 2023)
- NPR: Vanuatu Government Cyberattack (December 2022)
- The Diplomat: Vanuatu Cyberattack Analysis (December 2022)
- The Record: Palau Health Ministry Ransomware (March 2025)
- Asia Pacific Report: Tonga Cybersecurity Expert Analysis (July 2025)
- HackerNoon: DePIN Solutions for Tonga (July 2025)
- CSIDB: Tonga Health System Cyberattack Database Entry
- Tonga Government Digital Transformation Framework