fast-growing, collaborative environments. These storage systems boasted different degrees of data availability and data security and protection from loss. As Web2 grew in adoption so did the generation of Web2 data volume and density in many formats. This data could be large files, non-transactional, often created by a single user, and may be shared over some geographical distance. This design led to the reliance on central authorities to store the world's data.
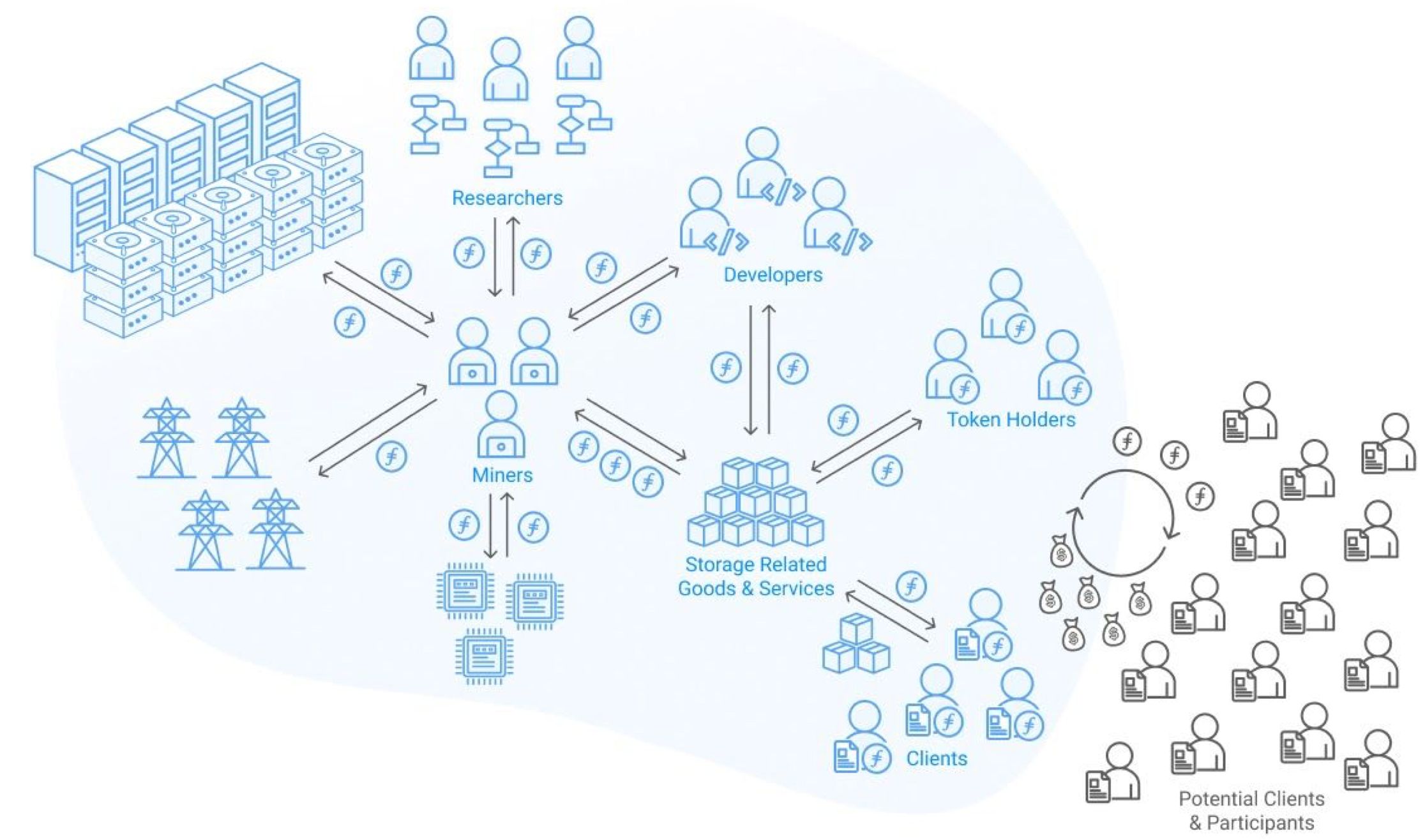
example, the decentralized storage network is designed with advanced
cryptographic methods and an incentive mechanism to encourage mass-scale consumption of p2p-first solutions.
Filecoin's protocol design and consensus mechanisms and how they incentivize decentralized storage. Before we start unveiling the
magic of decentralized storage we will first explore the limitations
in traditional storage solutions.
Limitations in Traditional Data Storage
based addressing system. Central servers keep a list, or directory of the location of data elements for example path and filenames of each data structure. These primary addresses are Uniform Resource Locators (URLs). Servers use these directories to locate data and retrieve it. Information at given locations can usually be altered or completely overwritten without
modification trackers on the servers.
resilience, as the network use cryptographic hashes at its core which
eliminates problems linked with address changes like 404 Err. Data on this system is secure from alterations which result in hashes changes. Traditional data storage also have several other limitations including:
- System Vulnerabilities: Vulnerabilities on these systems include limitations to network connectivity and bottlenecks of high traffic.
- Power Distribution: Centralization cause unhealthy disparities in power distribution which can lead to censorship.
- Fault Tolerance: Without fault tolerance set up and back-up servers, data losses can
happen in cases of hardware failures.
users/nodes joining the network which reduces latency and retrieval
time and simultaneously increases storage capacity.
Cryptographic Methods on Filecoin
miner and a client must be initiated and accepted by miner. To initiate a storage deal, a client submits a deal proposal using a Piece CID which is wrapped with all the details of the deal parameters like the deal CID, miner ID, price, and duration.
sector (the storage unit on Filecoin), seal it and start submitting proofs to the network. The storage deal will now be live on the network. Filecoin
uses two cryptographic proofs to verify storage on the network, Proof of Replication (PoRep) and Proof of Spacetime. (PoSt).
Proof of Replication (PoRep)
unique copy or replica of data. The process happens once when data is first stored by miner in two steps filling sector and sealing sector.
the sector is full an UnSealedSectorCID is generated. This CID, a Commitment of Data or CommD is the root node of all the Piece CIDs in the sector.
process making it difficult to spoof. The UnSealedSectorCID or CommD
is encoded through a sequence of graph and hashing processes to
create a unique replica.
Proof of Spacetime (PoSt)
dedicate storage space to the same data over time. This process requires Merkle Inclusion Proofs which are regular checks to ensure that a random selection of encoded data is present at the right location.
spacetime at any point, they will be penalized.
Zk-SNARKs
“Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge". Zk-SNARKs let us prove that a proof has been done correctly without having to reveal the details of the proof itself or the underlying data on which it's based.
end product is small and the verification process is very fast. Zk-snarks keep the chain small and reduce the time needed for verification.