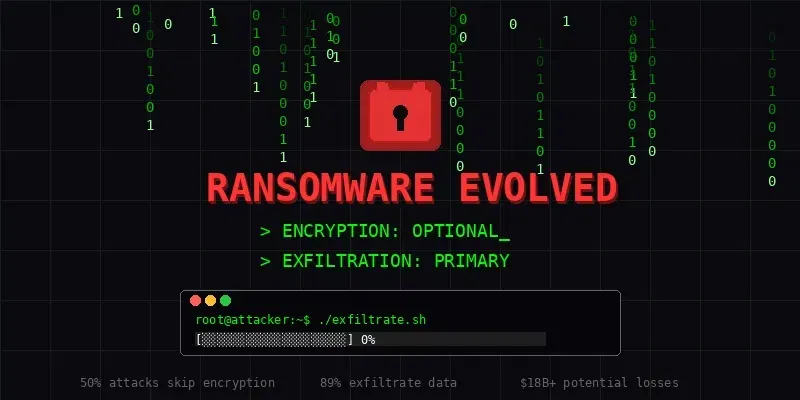
Ransomware is evolving from "lock your files and demand payment" to "steal everything and threaten to leak it." About 50% of attacks now skip encryption entirely. Payments are declining, but the damage is worse than ever. Welcome to 2026.
The Old Playbook Is Dead
Remember when ransomware was simple? Attackers encrypt your files, you pay up (or don't), life moves on.
Those days are over.
In 2025, something shifted. Groups like Cl0p stopped bothering with encryption altogether. Why waste time locking files when you can just take them?
Here's the brutal math:
- 89% of ransomware attacks now include data exfiltration
- ~50% of attacks are pure theft-and-extortion — no encryption at all
- Manufacturing alone faced $18+ billion in potential losses in 2025
The result? Your backups are useless. You can restore your systems all day long — it doesn't un-steal your customer database.
Why Attackers Ditched Encryption
Encryption is noisy. It triggers alerts. It requires complex malware that security tools are trained to catch.
Data exfiltration? That's just... traffic.
Modern attackers use tools already in your environment:
- Azure Copy — blends with normal cloud backup operations
- Rclone — looks like legitimate data synchronization
- FileZilla — standard FTP client, nothing to see here
By the time you notice something's wrong, they've been camped in your network for weeks. Sometimes months.
One security researcher put it bluntly: "When attackers only exfiltrate data, most organizations can't determine what was stolen — or whether it was stolen at all."
Attackers know this. Fake exfiltration campaigns are now a thing — groups claiming to have your data when they don't, because you literally can't prove them wrong.
The Scattered Spider Effect
If you want to understand where ransomware is heading, look at Scattered Spider.
This isn't some shadowy Russian syndicate. It's largely teenagers and young adults from the US and UK who grew up in gaming communities like Discord and Roblox. Security researchers call them "advanced persistent teenagers."
Their rap sheet since 2022:
- $1 trillion+ in market cap of targeted companies
- $115 million+ in confirmed ransom payments
- Victims include MGM Resorts, Caesars, Marks & Spencer, Coinbase, and Snowflake customers
- 120+ corporate breaches across retail, airlines, insurance, and banking
Their secret weapon? They speak English. Natively.
While Russian groups rely on broken-English phishing emails, Scattered Spider members call your help desk, impersonate new hires, and chat up employees on Slack. They study your internal lingo. They know who to ask for admin access.
One member allegedly hacked a federal judge's email account while in jail — by calling and impersonating another judge to reset the password.
Several members have been arrested, including a 17-year-old who surrendered to Las Vegas police in September 2025. But arrests haven't slowed the group. Its decentralized structure means new members cycle in constantly.
The kicker? They're now collaborating with Russian ransomware gangs like Akira and DragonForce. Teenage social engineers meet professional malware operators.
The Triple Extortion Era
Remember "double extortion"? Encrypt files and threaten to leak data.
That's table stakes now. Welcome to triple extortion:
- Steal your data
- Encrypt your systems (optional)
- DDoS your infrastructure if you don't pay fast enough
- Contact your customers, partners, and employees directly to create public pressure
The Cl0p group pioneered this approach. When a victim refuses to pay, they don't just post data on their leak site. They email the victim's employees. They contact journalists. They call customers and tell them their data is compromised.
It works. Victims pay even without encryption, driven by:
- Regulatory exposure — GDPR, HIPAA, SEC rules don't care if data was encrypted. If it was accessed, you report it.
- Reputational damage — Customers don't distinguish between "they encrypted our files" and "they stole our customer database"
- Legal liability — Lawsuits from affected employees and customers are spiking
The Global Expansion
Here's a stat that should concern everyone: 2026 is expected to be the first year non-Russian ransomware actors outnumber Russian ones.
This isn't because Russian groups are declining. It's because the playbook has spread everywhere.
Ransomware-as-a-Service (RaaS) platforms have made sophisticated attacks available to anyone willing to pay. You don't need to write malware — you rent it. You don't need infrastructure — the RaaS operator provides it. You just need targets.
The result is a Cambrian explosion of new groups:
- FunkSec — Using AI-generated code for low-cost, high-volume attacks
- NightSpire — Started with pure exfiltration, later added encryption
- SafePay — Took down Ingram Micro for nearly a week, causing an estimated $136M/day in losses
Law enforcement disruptions barely slow things down. When RansomHub shut down in April 2025, its affiliates simply moved to Qilin — which became the most active ransomware group for six consecutive months.
The Insider Recruitment Problem
The latest escalation: ransomware groups are recruiting your employees.
Not metaphorically. Literally.
Groups are increasingly using native English speakers to contact corporate insiders directly. The pitch is simple: plant malware or share credentials, get a cut of the ransom.
One researcher documented an increase in insider recruitment attempts throughout 2025. If layoffs continue in 2026, this trend will accelerate. Disgruntled employees with system access are a gold mine.
In one case, attackers hired a gig worker through a legitimate platform to physically visit an office and plug in a malicious USB drive. The gig worker had no idea they were working for hackers — they thought it was a routine IT task.
What Actually Works
Good news: ransomware payments are declining. The combination of better backups, improved incident response, and organizations simply refusing to pay is working.
Bad news: attackers don't care. They're making it up in volume and pressure tactics.
What's actually moving the needle:
1. Assume Exfiltration, Not Just Encryption Your backup strategy is insufficient. You need visibility into outbound data flows — especially cloud services and third-party sync tools. If you can't see data leaving, you can't stop it.
2. Identity Is the New Perimeter Attackers "log in" rather than "break in." Stolen credentials, phished passwords, and social-engineered help desk resets are the entry points. Multi-factor authentication isn't optional — and SMS-based MFA isn't real MFA.
3. Verify Everything, Trust Nothing If someone calls your help desk claiming to be an employee, verify their identity through a separate channel. Scattered Spider's entire playbook depends on humans trusting other humans who sound legitimate.
4. Segment Ruthlessly When (not if) attackers get in, limit the blast radius. A compromised marketing intern shouldn't have access to customer payment data.
5. Practice Disclosure, Not Just Recovery You need a crisis communications plan. When attackers start emailing your customers, what do you say? Figure that out before it happens.
The Road Ahead
The ransomware ecosystem isn't collapsing — it's professionalizing. Groups operate like businesses with org charts, customer support (for victims paying ransoms), and affiliate programs.
Payments may be declining, but total costs are rising. A ransomware attack now averages $1.8 to $5 million in total impact — including downtime, recovery, legal fees, and reputational damage.
The groups that succeed in 2026 won't necessarily have the best malware. They'll have the best:
- Social engineering — Native speakers who can manipulate humans
- Timing — Targeting organizations during acquisitions, layoffs, or holiday weekends
- Pressure campaigns — Turning stolen data into public relations nightmares
Encryption was just the opening act. The main show is psychological warfare.
Welcome to the new era of ransomware. Bring your incident response team.