Edward Snowden's revelations in 2013 made it clear that the internet we trusted was never truly confidential. Since then, a decade has passed by, and a new generation of decentralized technologies has challenged the traditional system. These technologies highlight the importance of decentralization and the confidentiality of personal information.
However, for all the potential of anonymity and censorship resistance, one inconvenient truth remains: pseudonymity.
Most decentralized apps and networks today treat confidentiality and anonymity as an afterthought. Something of an ‘additional feature’. Confidentiality, when treated as an all-or-nothing switch, can be painfully slow, user-unfriendly, and even risky.
Let’s face it. Many applications that
That's where
How Does BelNet Work?
BelNet relies on a decentralized network of
It masks the user IP, relays the user data at least through 3 different masternodes before passing it on to an exit node run by the Beldex community.
BelNet encrypts the data at each stage of transit (at every masternode hop). The network of masternodes are sufficiently decentralized so as to prevent DDoS, man-in-the-middle, and deanonymizing attacks. Its robust encryption standards also prevent data interception and data theft.
More information on how BelNet works can be found here:
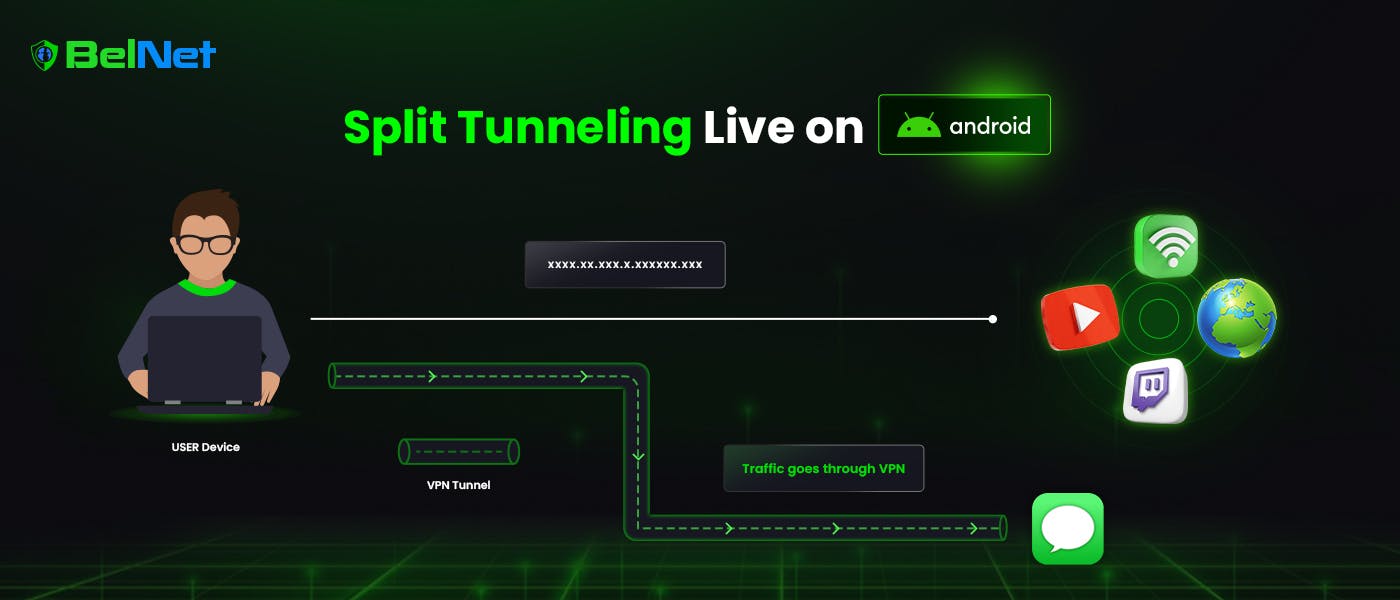
The focus of today’s article is Split Tunneling, a feature that’s been on the BelNet team’s checklist for quite some time.
Understanding Split Tunneling in Confidential Networks
Split tunneling is a networking technology that allows you to control which parts of your internet traffic are routed through a safe, encrypted tunnel (similar to a VPN) and which go directly to the internet. The split tunnel separates data based on user-preference before routing them.
It prevents all of your data from passing through the same confidentiality-preserving route.
But why do we need split tunneling?
Selective routing is especially important in decentralized networks like BelNet, where traffic is routed through a chain of masternodes rather than centralized servers.
It allows users to safeguard sensitive data (such as identification credentials or encrypted communication) while still having fast access to public content (such as viewing YouTube, streaming on Twitch or browsing Wikipedia).
While BelNet masternodes and exit nodes support streaming videos in high quality and resolution, our users have suggested that certain apps just do not require the layer of confidentiality offered by an onion-network and bypassing them would potentially reduce the load on BelNet. Heeding to popular opinion, Split Tunneling is being implemented.
Why Full Tunneling Isn't Always Useful for Blockchain Users
Full tunneling, where everything is sent through a secure network, may seem like the best way to route traffic in a confidential dVPN.
But in reality, it is much like hoping every car and truck in a city can travel along the same street at once: this system is inefficient and likely to lead to breakdowns, especially during peak hours.
The drawbacks:
Routing every data packet across numerous nodes causes delays, particularly in real-time applications. Certain nodes might be overloaded due to high demand.
Decentralized nodes also have bandwidth restrictions. While we try to ensure minimum standards, forcing them to handle all user traffic leads to unnecessary congestion.
How BelNet Implements Split Tunneling
BelNet allows users to select what data is encrypted and what isn't on the application layer, balancing confidentiality and performance. Only important traffic (traffic through apps selected by the user) may be routed through BelNet's secure masternode network, while normal browsing or streaming is bypassed for speed.
User-Friendly Use Cases: From Streaming to Secure Identity Access
Suppose you're a freelance developer working remotely from a cafe:
- You launch a GitHub source - An app that you’ve set to bypass the tunnel. So BelNet sees it as safe and skips the tunnel.
- You log into your cryptocurrency wallet - You’ve set this app to go through the tunnel. BelNet takes over, encrypting the request through its masternode layer.
- A software upgrade begins in the background and continues unrestricted outside the tunnel.
- On BChat, you receive an encrypted message that has been routed safely and with almost no latency.
Benefits Beyond Confidentiality: Speed, Reliability, and Usability
VPNs and confidentiality solutions are typically assessed based on how much they slow down. BelNet changes the process.
- Speed: Non-sensitive communication is not slowed by encryption, allowing you to browse at regular rates.
- Reliability: Less traffic in the masternode network equals higher uptime for important services.
- User Experience: The invisible split eliminates the need to worry about controlling your confidentiality all the time—it is configured once and adjusts continually.
Decentralized tunneling networks that enable split tunneling have quicker average load times for general content than those with complete routing.
Closing Thoughts
Split tunneling in BelNet is more than simply a technical feature; it is a concept. It's about knowing that the internet isn’t black or white. Certain data is precious. Some are not. However, users should not need to know which is which.
Beldex enables BelNet to automatically route data based on decisions made by you - giving you complete control over your confidentiality.
Selective confidentiality is not a compromise. It's the intelligent development of secure internet access, providing our users with speed, safety, and simplicity.