As a bug bounty hunter and occasional CTF player, I often need to simulate HTTP requests quickly, safely, and without exposing data to third-party servers.
Most people use tools like Postman, Insomnia, or curl. They’re great — but sometimes they’re overkill, or just not usable in highly restricted environments.
The Problem
As a security researcher and bug bounty hunter, I often needed a single, lightweight tool that would allow me to simulate raw HTTP requests directly in the browser — with no backend, no logs, and no internet connection.
I wanted something that works 100% offline, requires zero dependencies, and gives me full control over crafting requests.
Manually copying and pasting curl commands or switching between multiple tools just to test a webhook or endpoint felt inefficient and tedious.
More importantly, I needed to be able to:
- Modify request headers freely without limitations.
- Switch between methods (
GET,POST, etc.) instantly. - Quickly decode or encode payloads on the fly.
So I decided to build something that includes everything I personally needed, all in one interface.
Built-In Tools That Help in Real-World Pentesting
To streamline security testing, I added a dedicated Tools section that includes:
Encoding and Decoding Tools
Quick, browser-native conversions for common data formats:
- ✅ Base64 encode/decode
- ✅ URL encode/decode
- ✅ HTML entity encode/decode
- ✅ JWT decoder with structured output
Payload Generator
A curated set of ready-to-use payloads to test various security flaws within seconds:
- XSS (Cross-Site Scripting)
- SQL Injection
- Command Injection
- LFI (Local File Inclusion)
- SSRF (Server-Side Request Forgery)
- RCE (Remote Code Execution)
- SSTI (Server-Side Template Injection)
- XXE (XML External Entity)
- CRLF Injection
- JSON Injection
- Host Header Injection
- Windows-specific LFI payloads
These payloads are immediately accessible and can be dropped into your request body or parameters, saving time during recon and testing.
The Solution: CyberPost
To solve these limitations, I created CyberPost — a lightweight, browser-based HTTP testing tool designed specifically for security researchers, bug bounty hunters, and developers who need full control in isolated environments.
Here’s what makes CyberPost stand out:
- 🌐 No backend required: All operations happen locally in your browser. No data is sent externally. No telemetry. No tracking.
- 📴 Works fully offline: You can simply open the HTML file — even in an air-gapped or restricted environment — and send raw HTTP requests to local services or targets.
- 🧰 Fully customizable: Modify request method, headers, and body as needed. Add tokens, tweak content types, simulate custom clients — it’s all in your hands.
- 🧪 Made for security testing: Whether you’re testing webhooks, fuzzing an API endpoint, or mimicking mobile app behavior, CyberPost gives you the flexibility and privacy to do it fast and locally.
- 🧠 Built-in Tools section: Encode/decode Base64, URL strings, JWTs, HTML entities — right in the same interface.
- 💣 One-click payload injection: Access a curated list of preloaded security payloads (XSS, SQLi, RCE, SSRF, etc.) for instant vulnerability testing.
CyberPost was built out of necessity — now it’s open source and ready for the community.
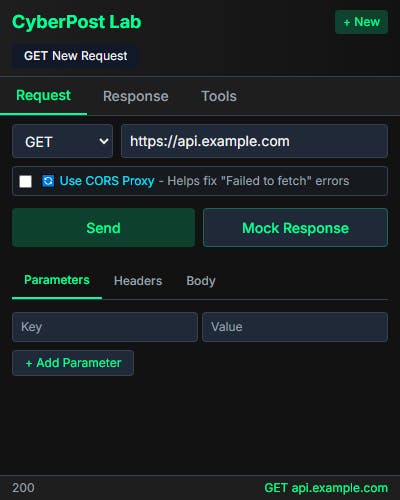
Here’s what it looks like:
Final Thoughts
CyberPost was born out of necessity — not as a replacement for full-featured tools like Postman, but as a focused alternative for environments where simplicity, privacy, and full offline control are essential. If you often work in isolated labs, air-gapped systems, or just need a lightweight utility that gets out of your way and lets you test raw HTTP requests fast, I invite you to give CyberPost a try.
It’s open source, self-contained, and built with the needs of real-world security researchers in mind.
🔗 GitHub:
🔗 CyberPost available on Firefox Add-ons Store!
🔗CyberPost available on the Chrome Web Store!