As part of setting up HTTPS using an SSL certificate for a website, I used the provided PEM (.pem) file (more on the file type and what it contains later). The certificate works well on my macOS, gets added to the keychain and once I trust the certificate everything works as expected - Open the browser and launch the website https://<Website>:443. Voila! it works.
Now, I shared the same .pem file along with the .key file with a Windows user. The user imports the certificate to the Microsoft Management Console (mmc), opens a browser and tries to access the website https://<Website>:443. The response is sorry this connection is not secured. Hmmm, what went wrong. What am I missing?
Let’s take a step back and understand certificates and their formats
Understanding SSL Certificates and their Various Formats
This section provides an overview of SSL (Secure Sockets Layer) certificates, their purpose, and the different file formats they commonly come in, such as .pem, .pfx, and .p12. Let’s explore the key differences between these formats and when each of these formats should be used.
What is an SSL Certificate?
An SSL certificate is a digital certificate that authenticates a website's identity and enables an encrypted connection. When a browser connects to a website secured with SSL, the server's SSL certificate is verified. This verification process confirms that the website is who it claims to be and that the communication between the browser and the server is encrypted, protecting sensitive data like passwords, credit card numbers, and personal information.
Common SSL Certificate File Formats
SSL certificates are stored in various file formats, each with its own structure and purpose. Here's a breakdown of the most common formats:
1. PEM (.pem, .crt, .cer)
Description: PEM (Privacy Enhanced Mail) is the most common format for SSL certificates. It's a text-based format that uses ASCII encoding and contains the certificate data encoded in Base64. PEM files can contain one or more certificates, including the server certificate, intermediate certificates, and the private key.
Content: A PEM file typically contains the following:
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----block for the certificate itself.-----BEGIN PRIVATE KEY-----and-----END PRIVATE KEY-----block for the private key (if included).- Intermediate certificates may also be included in separate blocks.
Usage: PEM files are widely used by web servers like Apache and Nginx. They are also commonly used for storing individual certificates and keys.
Example :
-----BEGIN CERTIFICATE-----
MIIGZTCCBE2gAwIBAgIJAJtxa2snhjXOMA0GCSqGSIb3DQEBCwUAMI...
-----END CERTIFICATE-----
-----BEGIN PRIVATE KEY-----
MIIEpQIBAAKCAQEAw9K+J92tW9mdj0N/y/1q1w0/iJ0+Vq9z8...
-----END PRIVATE KEY-----
2. DER (.der)
Description: DER (Distinguished Encoding Rules) is a binary format for storing SSL certificates. It's the binary equivalent of a PEM file.
Content: DER files contain the raw binary data of the certificate.
Usage: DER files are less common than PEM files but are sometimes required by Java-based applications.
Conversion: DER files can be converted to PEM files using OpenSSL:
openssl x509 -inform der -in certificate.der -out certificate.pem
You need to download and install openSSL on your machine.
3. PFX (.pfx, .p12)
Description: PFX (Personal Exchange Format) is a binary format that can store the server certificate, any intermediate certificates, and the private key in a single, password-protected file. .p12 is essentially the same format, often used interchangeably.
Content: A PFX file contains the entire certificate chain and the private key, all encrypted with a password.
Usage: PFX files are commonly used by Windows servers (IIS) and for importing certificates into email clients and other applications.
Security: PFX files are more secure than PEM files because they encrypt the private key with a password.
Conversion: PFX files can be converted to PEM files using OpenSSL:
openssl pkcs12 -in certificate.pfx -out certificate.pem -nodes
The -node option removes the password protection from the private key in the PEM file. Omit this if you want to keep the private key encrypted.
Key Differences
|
Feature |
PEM |
DER |
PFX/P12 |
|---|---|---|---|
|
Format |
Text-based (Base64 encoded) |
Binary |
Binary |
|
Content |
Certificate, Private Key (optional) |
Certificate |
Certificate Chain, Private Key |
|
Security |
Private key may be unencrypted |
Private key not included |
Password-protected encryption |
|
Common Usage |
Web servers (Apache, Nginx) |
Java-based applications |
Windows servers (IIS), Email clients |
|
File Extensions |
.pem, .crt, .cer |
.der |
.pfx, .p12 |
The next ultimate question would be which format should I choose
Choosing the Right Format
The choice of SSL certificate format depends on the specific requirements of the application or server you are using.
- PEM: Use PEM format when you need individual certificate files and private keys, especially for web servers like Apache and Nginx.
- DER: Use DER format when required by specific applications, such as some Java-based systems.
- PFX/P12: Use PFX/P12 format when you need to store the entire certificate chain and private key in a single, password-protected file, particularly for Windows servers (IIS) and importing into email clients.
How can I fix the connection is not secured on a browser running on Windows?
Let’s talk about the problem in-depth here. On macOS, you double-click on the provided PEM file and it launches the keychain, the certificate is added to the keychain, you expand the certificate and Trust the certificate (Always). Voila!! you are all good here.
As mentioned above, .pfx / p12 is the preferred format on Windows. You can either convert the provided PEM to PFX or use the provided format. You will be prompted for a password.
openssl pkcs12 -export -out mycert.pfx -inkey mycert.key -in mycert.pem
On Windows OS, it’s different. Along with the PEM file, you would need the rootCA and IntermediateCA certificates. These two certificates are part of the chain of trust components.
The chain of trust is a fundamental concept in digital security that underpins the reliability and authenticity of SSL/TLS certificates used to secure online communications. It establishes a hierarchical structure of trust, starting from a trusted root Certificate Authority (CA) and extending down to the end-entity certificate used by a website or service.To understand the chain of trust, read this article.
Before you continue further, you must have these three certificates from the provider to enable HTTPS (SSL) on your Windows OS.
- Root Certificate Authority (Root CA)
- Intermediate Certificate Authority (Intermediate CA)
- End-entity Certificate (Server or Client Certificate)
Without the root and intermediate CA certificates, you will see the following warnings when you import only the client certificate (PEM) file to Windows OS mmc ( you will learn this in the next section)
Windows does not have enough information to verify this certificate
The issuer of this certificate could not be found
Prepare the certificates
This article expects that the Root CA and Intermediate CA are in .cer format. If not, here’s how you can
- On your Windows OS, open a notepad or any other text editor.
- Open the provided Root CA and Intermediate CA files (maybe in PEM format).
- Copy the contents of the Root CA and include the
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----. - Create a new file rootCA.cer, paste the copied contents and save the file. Follow the steps to create a new IntermediateCA.cer.
Import and manage certificates in mmc
Microsoft Management Console (MMC) helps to create, save and open administrative tools, called consoles, which manage the hardware, software, and network components of your Microsoft Windows operating system. MMC runs on all client operating systems that are currently supported.
- To launch mmc, search mmc and run it as an administrator
- Create an mmc console with certificates snap-in by clicking on File → Add/Remove Snap-in.
-
Click on certificates and then on Add >
- Select Computer Account and click Next
- Select Local Computer and click Finish
- On the snap-in, click OK
4. Import rootCA.cer to Trusted Root Certification Authorities by right clicking → All Tasks → Import
- Select Local Machine and click Next.
- Browse the location of rootCA.cer on your machine and click Next.
- Place the certificate in the Trusted Root Certification Authorities store and click Next.
- Click on Finish to import the certificate successfully.
- Repeat the above steps to import the intermediateCA.cer certificate to the Intermediate Certificate Authorities store
Import the client certificate (cer / pem / pfx)
- If you have a .cer file, double click on the file to open a prompt and install the certificate.
- If you are provided with a .pfx file, double click on the file to launch the Certificate Import Wizard → Choose Local Machine → Provide the password associated with the file (ask your certificate provider) and complete the import.
- If you are given a .pem file, launch mmc, right click on Personal under certificates and import the certificate similar to the way you do install the root or intermediate CA.
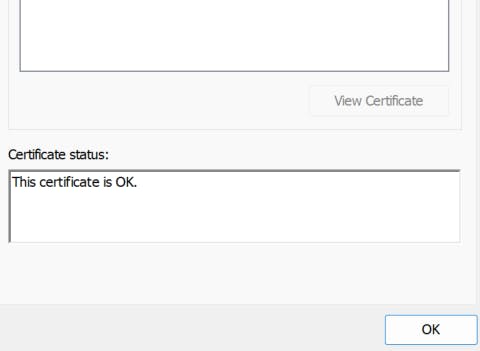
- Once all the certificates - root, intermediate and client(.pfx /.cer/ .pem) are imported. When you double click on the client certificate, you should see the following
Conclusion
Whichever format of the client certificate you receive, it’s key to check the integrity of the file. Once you are sure that you have received the right certificate, based on the Operating System, you may need to ask for additional certificates like root or/and intermediate certificates. Rotating the client certificate is key to the security of the system. Forgot to mention, now you can open your browser and enter https://<website>:443 with a note saying your connection is secured. If your certificates are not working as expected, cross-check with your provider for the certificates that match your domain even if it is wild card certs like *.example.com